NATO’s deterrent power faces historic tests across kinetic and digital domains. The war in Ukraine has brought hybrid warfare to the fore and coincided with a steady uptick in cyber operations targeting NATO members and their allies. Attacks against civilians and critical infrastructure have also increased, despite growing global consensus that such attacks violate international humanitarian law. Meanwhile, the expanding use of artificial intelligence (AI) is enhancing cyberattacks and cyber deterrence alike, with the potential to change the future of hybrid warfare. As NATO marks its 75th anniversary, this issue brief highlights opportunities to develop and implement effective deterrence strategies accounting and preparing for the role of AI. Focusing on the most destructive cyberattacks, the analysis identifies critical deterrence gaps and presents cross-sectoral recommendations to strengthen deterrence.
Cyber deterrence strategies can be divided into two main approaches: those reducing the perceived benefits of attacks, and those increasing their perceived costs. A strategy of denial seeks to reduce the incentive to attack by making digital systems resilient, such that they can withstand attacks while suffering a minimal loss of capabilities. For example, cyber defense exercises and rapid response teams can minimize the damage inflicted by cyberattacks and quickly recover access to targeted services. A strategy of punishment seeks to impose consequences on attackers that outweigh any potential benefits of an attack, and to hold attackers accountable for their actions. One prerequisite to punishment is accurately identifying the attacker, also known as attribution. Examples of punitive consequences include ongoing efforts to clarify and enforce international law on cyber operations, as well as NATO warnings that “significant malicious cumulative” cyberattacks on a member state could trigger Article 5 of the North Atlantic Treaty.
AI Offers New Capabilities to Both Attackers and Defenders in Cyberspace
Cyber attackers are increasingly finding new ways to apply AI to enhance the scale, sophistication, and anonymity of their operations while reducing associated costs. For example, AI is reportedly driving a surge in phishing attacks; a 2023 report found that 75 percent of 650 surveyed cybersecurity professionals had witnessed an increase in attacks over the prior year, of whom 85 percent attributed the rise to AI. These capabilities present new threats to banks, power grids, hospitals, elections, and other forms of critical infrastructure commonly targeted by state-backed hackers, as well as to sensitive data or intellectual property. By creating an environment in which it is cheaper and easier to attack than to build effective defenses, AI has the potential to escalate hybrid conflicts and inflict significant harm on civilians.
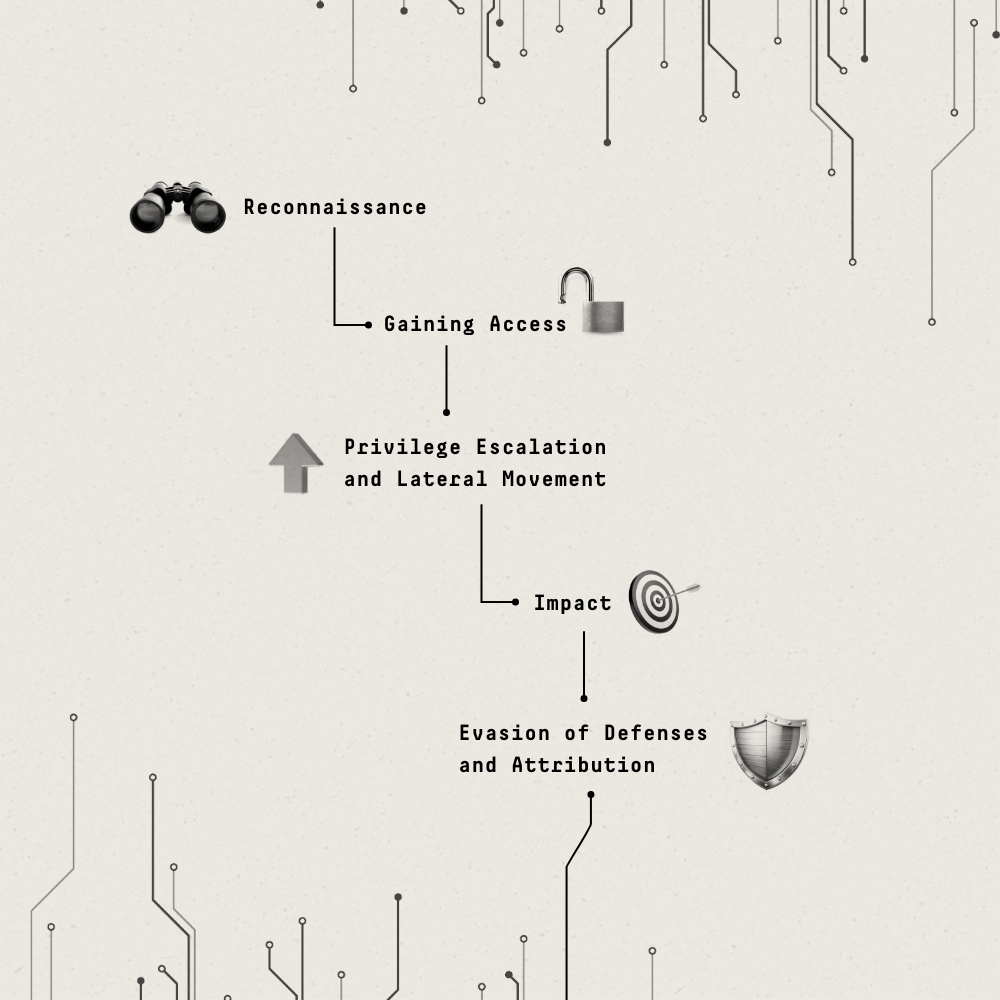
Assessing AI’s impact across the lifecycle of a cyberattack
The lifecycle of cyberattacks can be broken into phases. Here, the MITRE ATT&CK framework is consolidated into five stages, representing a simplified timeline of how AI impacts cyber deterrence during an attempted attack.
Reconnaissance
Attackers collect intelligence that helps them select their targets and design the attack. This can include information about human targets used for social engineering, or technical information about targeted networks and software systems.
Attacker’s Use of AI
AI tools can be trained by attackers to collect sensitive information, for example via facial recognition across social media profiles. AI can also be trained to evade spam filters, craft realistic emails and documents, and mimic the voices or writing styles of trusted figures, which can improve social engineering methods like spear-phishing.
Defender’s Use of AI
Some AI tools are designed to distinguish between human- and AI-generated text, images, videos, or audio clips, which may help counteract AI-enhanced phishing campaigns. Other AI software uses predictive analytics to guess when and where future cyber threats may emerge. This capability can warn targeted organizations to deploy preventive measures before threats materialize.
Gaining Access
The attacker secures a foothold in their target’s information system. This can involve stealing credentials from legitimate users or exploiting a software vulnerability to obtain a “backdoor” into the system.
Attacker’s Use of AI
Applying AI to large password datasets can enable more accurate password guessing. Bots powered by machine learning may already be better and faster at solving CAPTCHA’s than humans, and AI can help circumvent firewalls or biometric security systems. AI-powered social engineering techniques can be used to steal user login credentials. AI can also create web content that may lure unsuspecting users to watering hole attacks.
Defender’s Use of AI
AI tools can quickly scan software to reveal insecure coding patterns or other weaknesses, then suggest more secure ways to code the same functions. This helps software designers patch vulnerabilities before releasing products and helps cybersecurity professionals eliminate backdoors before attackers exploit them. AI is also used in programs detecting unauthorized access to a system. By reducing false positives among flagged activity, AI can help cybersecurity professionals address the highest-risk cases.
Privilege Escalation and Lateral Movement
Steps an attacker takes after they initially breach a system to gain additional privileges needed for their aims, or to gain access to other systems that may be more sensitive or valuable.
Attacker’s Use of AI
Once inside an online system, attackers can use AI to identify insecure coding patterns, including by scaling a technique called “fuzzing,” making it faster to find and exploit weaknesses in the targeted systems.
Defender’s Use of AI
AI monitoring tools can scan massive network traffic logs to identify deviations from normal online behavior and flag malicious activity at machine speed. This shortens or eliminates attackers’ opportunity to inflict damage before their activity is uncovered, reducing the so-called “first-mover advantage” that can frustrate deterrence in other military contexts.
Impact
Actions an attacker performs to fulfill their goals within the system, such as encrypting or exfiltrating files, taking websites offline, or damaging targeted infrastructure.
Attacker’s Use of AI
When deploying an attack, AI can help coders generate sophisticated malware or ransomware that can increase the disruption and destruction inflicted by cyberattacks—for example, by more efficiently searching machines for critical data or intellectual property.
Defender’s Use of AI
AI is a crucial component of malware identification and data loss prevention software, which helps targeted organizations prevent or mitigate the destruction and disruption inflicted by cyberattacks.
Evasion of Defenses and Attribution
Attackers attempt to conceal their activity in order to avoid detection and attribution throughout the attack process.
Attacker’s Use of AI
AI coding can help attackers evade detection by constantly changing malware signatures. For example, a keystroke logger program called Black Mamba is programmed to call out to ChatGPT to generate new and different code each time it runs, frustrating efforts to detect code used in prior attacks. There are also concerns that AI could learn to mimic how human users type or behave online to evade security systems.
Defender’s Use of AI
AI-powered tools can identify patterns in hacker behavior, such as their timing, methods, and movement within an online system. In concert, these patterns may form a distinctive signature that can assist with detection and attribution. Defenders increasingly leverage digital forensics tools powered by AI to reconstruct cybercrime timelines and identify the culprits of cyberattacks, paving the way for accountability and deterrence.
Notwithstanding these emerging risks, AI also has the potential to be a crucial asset for cyber defense. AI can help monitor users’ activity online and detect and patch software vulnerabilities before attackers exploit them, boosting deterrence by denial. Meanwhile, sophisticated digital forensics tools could incorporate AI to detect and attribute cyberattacks, enabling deterrence by punishment. A wide range of cybersecurity products have incorporated AI for years. Unlike human monitors, automated systems are tireless and ever-vigilant, and automating more basic security tasks could help address the global cybersecurity skills shortage. As AI’s capabilities accelerate, deterrence will require cyber defenders to stay abreast of the latest techniques and keep pace with attackers’ evolving technological sophistication.
Effectively deploying these powerful AI monitoring and forensics tools will require deepening public-private, civil-military, and allied nation collaboration. The private sector owns and operates 80 percent of global cyber infrastructure and is usually first to detect and respond to attacks. For this reason, the Enhanced NATO Cyber Defence Pledge integrates the political, military, and technical components of cyber deterrence with private-sector capabilities. Similarly, sharing information between states and independent experts can help fill evidence gaps, triangulate who is responsible, and increase the credibility of accusations through corroborating sources. The Five Eyes intelligence alliance has used this strategy to collectively attribute Chinese and Russian cyberattacks, while independent nonprofits offering transparent attribution services can augment the credibility of state accusations.
Mapping Hacker Groups’ Use of Large Language Models
In 2023, Microsoft partnered with OpenAI to document how five known hacking groups were using large language models (LLMs) to enhance their operations. Their research found that attackers used LLMs during the reconnaissance stage and for help with coding and translation. However, LLMs are only one form of AI and other research suggests that AI’s impacts may be most pronounced in the access and penetration phase of a cyberattack. Understanding of AI’s potential roles and impacts in cyber operations and hybrid warfare is still emerging.
Data source: Microsoft 2024a, Microsoft 2024b, The Hacker News 2023
Achieving Holistic Cyber Resilience Still Depends on the Fundamentals
While AI-powered cybersecurity can help level the technological playing field, AI alone is insufficient to ensure that digital systems remain resilient to cyberattacks. Cyber attackers exploit human error, which contributes to about 88 percent of data breaches. This risk could grow as AI phishing techniques become more prevalent. Effective deterrence will require tech developers to design and deploy new hardware and software with security in mind, putting as little burden as possible on end-users. An April 2023 report by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) urged tech manufacturers to prevent “customers from having to constantly perform monitoring, routine updates, and damage control” by making products secure “‘out of the box,’ with little to no configuration changes necessary and security features available without additional cost.”
Before attacks occur, states and allies can leverage rehearsals, hackathons, red-teaming exercises, and other initiatives to develop coordinated response strategies. They can also invest in rapid response teams to quickly recover affected capabilities and minimize disruption. The Computer Emergency Response Team of Ukraine has proven highly effective against Russian cyberattacks as part of a broader cross-sectoral response. However, equivalent teams run by the NATO Cyber Security Centre were unable to remedy the cyberattacks suffered by Albania in 2022, and may need reform to become more agile, streamlined, and proactive.
Current collective cyber defense strategies may be too slow to effectively deny or deter attacks. For example, decisions to deploy a NATO cyber response team currently require a formal request process followed by consensus among all 32 member states, which would likely take too long to prevent damage by attackers. At the 2023 Vilnius summit, NATO committed to Virtual Cyber Incident Support Capability (VCISC) to enable remote international mitigation of malicious cyber activities. To succeed, the VCISC will need a streamlined structure capable of deploying responders quickly, as well as trust among participating stakeholders to share the sensitive information needed to diagnose attacks and get cyber networks back online. At times, activating response teams from a single trusted country may be faster and more effective than mobilizing multinational coalitions, such as when teams from the United States aided Albania in 2022.
Imposing Meaningful Consequences on Cyber Attackers Requires Developing Proportional Retaliation Options
Effective cyber deterrence requires coupling resilience and attribution with credible punishments for cyber attackers. One avenue for accountability is international law, but ongoing efforts to clarify the application of international law to the cyber realm face important unanswered questions. The increasing involvement of civilians in cyber operations blurs legal distinctions between combatants and noncombatants and could expose civilians to military retaliation. Additionally, the increasing use of cyber mercenaries may require updating the legal definition of mercenary to hold states and their proxies accountable.
Until international law is more consistently enforced in the cyber realm, establishing accountability will require states to develop and impose proportional consequences on cyber aggressors. However, individual nations may prefer to establish different thresholds for risk and retaliation, presenting challenges for multinational alliances like NATO, which has remained vague about what cyberattacks could trigger Article V. Though there are defensible reasons for such strategic ambiguity, effectively punishing cyberattacks will require consensus on what qualifies as an attack. One way to define attacks is by target, such as when President Biden gave Russian President Vladimir Putin a list of 16 off-limits sectors of critical infrastructure. However, lists do not account for the relative severity of an attack, making it difficult to threaten proportional punishment. An “effects-based” definition represents a credible alternative, designating red lines and identifying retaliation measures based on the severity of economic, strategic, or humanitarian impacts a cyberattack inflicts.
Defining cyberattacks also requires categorizing “pre-positioning” operations that establish and maintain footholds in a digital system for future use, such as documented Chinese efforts to embed within U.S. critical infrastructure networks. These operations may have ambiguous intent, as similar techniques may be used for either espionage or more destructive cyberattacks, raising questions about whether they qualify as threats of aggression under international law. Credible deterrence will require defenders to not only threaten consequences in the abstract, but to calibrate and communicate which punishments—ranging from diplomatic denouncements, to sanctions, to kinetic military strikes, to retaliation in the cyber realm—are plausible in response to which forms of cyber aggression.
Any punishment strategy will need to overcome serious risks and obstacles. Drawing red lines can reduce flexibility in a crisis; should deterrence fail, leaders may feel pressured to escalate conflicts beyond their interests or democratic mandate. Punishing a specific incident may implicitly condone previously ignored or undetected attacks, which risks revealing intelligence gaps or normalizing low-level cyber operations capable of inflicting significant harm in the aggregate. Unilateral retaliation can also set precedents that undercut the global community’s ability to establish beneficial cyber norms. For example, when Israel destroyed Iranian nuclear centrifuges during the Stuxnet attack, it justified this act as a defensive measure serving national and international security. Nevertheless, the attack pre-empted a potential norm against cyberattacks on nuclear facilities, which could be especially dangerous or destabilizing.
Looking Ahead: Effective Cyber Resilience in the Age of AI
As capabilities evolve, AI has the potential to lower the costs and increase the effectiveness of cyberattacks, but also to lower the cost and effort of cybersecurity measures. To keep pace with these changing dynamics, NATO can strengthen cyber deterrence in the following ways:
- Assess and agree upon which cyberattacks are deterrable. AI’s potential to scale up attacks will require prioritization of deterrence in an increasingly crowded threat landscape. Punishments will be most credible and effective if they are proportional and reserved for the most destructive behavior in cyberspace.
- Engage allies, the private sector, and other stakeholders to rally a broad coalition of technical and political expertise. Harnessing the latest, most relevant AI capabilities demands continual collaboration among governments, multinational institutions, tech companies, and internet users. Likewise, attributing cyberattacks will be easier and more credible if allied intelligence agencies share information and pool resources.
- Invest proactively in AI monitoring and digital forensic technologies, and the training and preparation of rapid response teams. Keeping pace with the projected growth of AI-powered attacks will require matching their technological sophistication, trusting responders with sensitive data, and deploying response teams swiftly following an attack.
- Deploy hardware and software that is secure-by-design and by-default, especially in sensitive government systems. Hardening cyber defenses against increasingly advanced attacks requires minimizing reliance on fallible end-users and designing technology with built-in security features. AI tools that scan software for insecure coding practices can help developers patch vulnerabilities before products are released to the public.
- Establish and communicate multinational, proportional, and credible mechanisms through which to hold cyber attackers accountable. Until international law is more consistently adhered to and enforced, states will need to threaten and impose other forms of proportional retaliation for cyberattacks. This will require calibrating response options to each attack’s severity and geopolitical circumstances.
NATO’s Washington Summit is an opportunity to reaffirm and advance commitments to cyber deterrence, including by reviewing progress and obstacles to implementing the Enhanced NATO Cyber Defence Pledge agreed in Vilnius. By rising to meet the challenge of emerging technological threats, the alliance may endure for another 75 years and strengthen cyber defense well beyond the North Atlantic.
By Andrew Doris (Senior Policy and Research Analyst), Angeli Juani (Senior Policy and Quantitative Analyst), Isabel Schmidt (Senior Policy Analyst and Research Manager), and Dr. Mayesha Alam (Vice President of Research).
This issue brief was produced by FP Analytics, the independent research division of The FP Group, with support from Microsoft. FP Analytics retained control of the research direction and findings of this issue brief. Foreign Policy’s editorial team was not involved in the creation of this content.